Infosys McCamish Wins Final Approval—that headline has been making waves, especially among IT professionals, legal observers, and insurance clients. But let’s break it down in real-world terms. Infosys McCamish Systems LLC, a U.S.-based subsidiary of Indian IT services leader Infosys, has officially received final court approval for a $17.5 million class action settlement stemming from a massive cybersecurity breach in 2023. This wasn’t just a hiccup. The breach affected millions and raised tough questions about data security, accountability, and consumer rights. Now that the deal’s official, let’s dive into what actually happened, who’s impacted, and what we all can learn from this.
Table of Contents
Infosys McCamish Wins Final Approval
The Infosys McCamish case is a signal flare for every business that handles customer data—especially in high-trust industries like insurance and finance. Cybersecurity isn’t a “nice to have” anymore. It’s mission-critical, and the consequences for falling short are real. For consumers, it’s a reminder to stay alert, monitor your credit, and know your rights when your data is compromised. For businesses, it’s a chance to double down on protection and avoid becoming the next headline.

| Topic | Details |
|---|---|
| Company Involved | Infosys McCamish Systems LLC |
| Parent Company | Infosys Limited |
| Settlement Amount | $17.5 Million |
| Reason for Settlement | Cybersecurity incident in October 2023 |
| Final Court Approval Date | December 18, 2025 |
| Settlement Effective Date | Becomes binding after 30-day appeal period (by mid-January 2026) |
| Liability Admission | No – standard no-fault agreement |
| Number of Affected People | Estimated 6.1–6.5 million individuals |
| Compensation Available | Up to $6,000 in documented losses + 2 years of credit monitoring |
| Official Source | Infosys Statement (PDF) |
The 2023 Cyber Breach: What Went Wrong
In October 2023, cyber attackers successfully infiltrated Infosys McCamish’s systems, using ransomware to lock access and potentially exfiltrate data. The breach lasted several days—from October 29 to November 2—before systems were fully shut down and damage control began.
The data breach was particularly significant because Infosys McCamish handles insurance and retirement platform solutions, which means the compromised data included:
- Social Security numbers
- Date of birth
- Bank account information
- Insurance policy numbers
- Personal identifiers for policyholders
Public notifications confirmed that 6.1 to 6.5 million individuals were affected, including clients from well-known insurance brands. McCamish later admitted that this was a “targeted attack” and not a random incident.
How the Legal Process Unfolded?
Following the incident, multiple class action lawsuits were filed across U.S. federal courts. Plaintiffs accused Infosys McCamish of:
- Failing to implement sufficient data security controls
- Delaying breach notification beyond industry standards
- Negligence in safeguarding personally identifiable information (PII)
In March 2025, Infosys proposed a settlement of $17.5 million, not as an admission of guilt, but as a resolution to the growing legal storm. On December 18, 2025, the court finally gave its seal of approval.
If no one files an appeal within 30 days, the settlement becomes effective in mid-January 2026, resolving all claims associated with the breach.
What’s a Class Action Lawsuit (in Simple Terms)?
A class action is a special kind of lawsuit where one or more people represent a larger group with the same complaint. Instead of thousands of people filing individual lawsuits over the same issue, one unified case helps speed up justice, reduce court costs, and distribute settlements fairly.
So if your info was part of the breach, you could be entitled to part of that $17.5 million—but only if you file a valid claim by the deadline (expected to be around December 1, 2025).
Infosys McCamish Wins Final Approval Breakdown: How the $17.5 Million Will Be Used
Here’s how the settlement money is being allocated:
1. Cash Compensation (Up to $6,000 per claimant)
Claimants with documented financial loss—such as fraudulent withdrawals, legal fees, or credit recovery services—can receive up to $6,000 in reimbursement.
2. Free Credit Monitoring (2 Years)
All eligible claimants will receive two years of professional credit monitoring, helping them detect potential fraud early.
3. Residual Payments
If there’s leftover money after payouts and fees, claimants may receive residual cash payments (likely between $30–$100 depending on participation rate).
4. Administrative & Legal Costs
A portion of the fund goes toward:
- Class counsel legal fees
- Court costs
- Settlement administrator fees
How to Know If You’re Eligible?
If your information was involved in the breach, you likely received a notification letter or email from either Infosys McCamish or one of its insurance partners. These notices include a unique claim number or instructions for filing.
If you didn’t receive anything but think you were affected, check:
- Past insurance accounts processed through McCamish
- Notices from banks or financial advisors
- The official settlement website (to be announced soon)
Industry Impact: Why This Settlement Is a Big Deal
The Infosys McCamish case isn’t just about one breach—it reflects broader issues in the IT services and insurance tech industry.
A Wake-Up Call for the Insurtech Sector
Companies that handle sensitive customer data must go beyond basic compliance and implement next-gen cybersecurity frameworks. The insurance sector in particular deals with legacy systems that are vulnerable to modern threats.
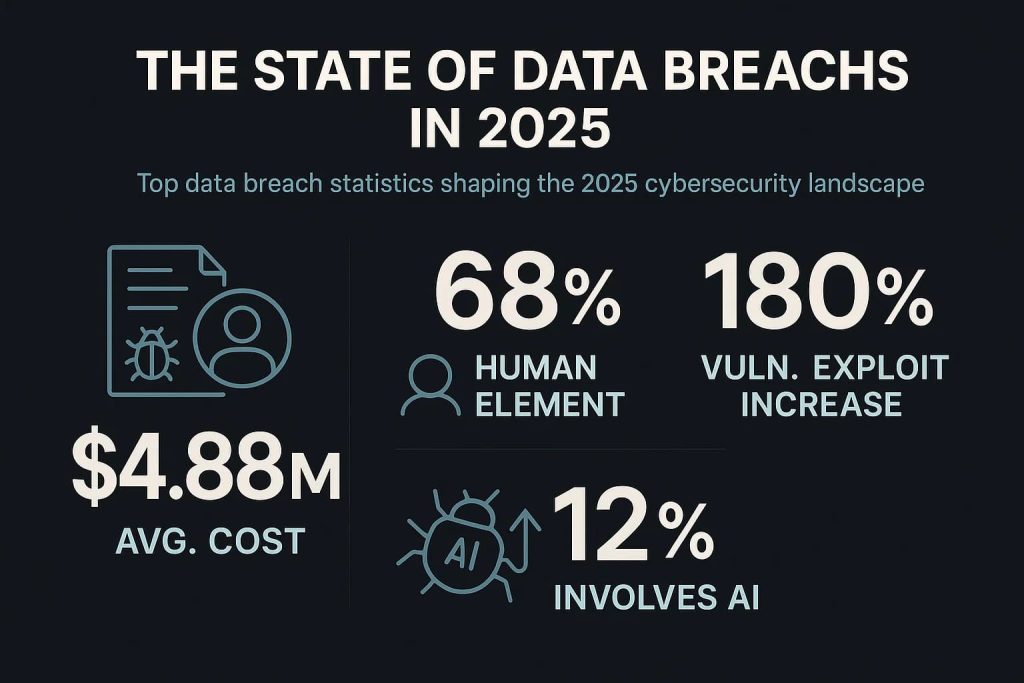
Rising Frequency of Attacks
According to the Identity Theft Resource Center, 2023 saw a record-high number of data breaches in the U.S., with over 3,200 confirmed incidents, up 15% year-over-year.
Legal Precedents
This settlement reinforces that third-party IT providers can be held legally liable for client data breaches, even if they’re not the source of the attack. Vendors and partners must now build zero-trust frameworks and have cyber insurance in place.
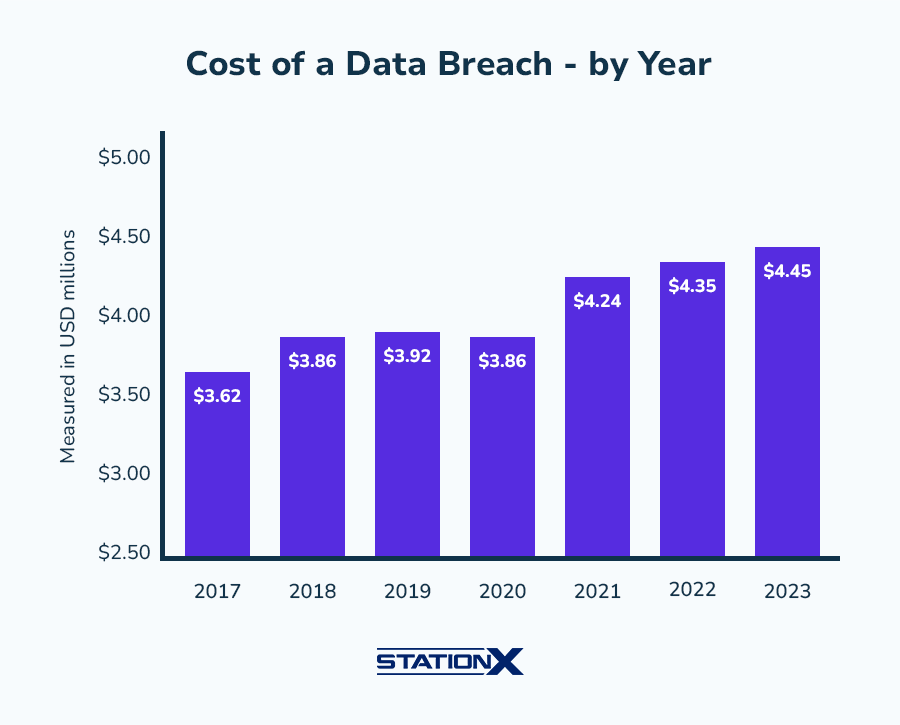
How Can Businesses Learn From This?
Here’s what IT leaders, SMB owners, and C-suite executives should take away:
1. Audit Your Vendors
Don’t assume your vendors are secure. Review their:
- Security certifications (SOC 2, ISO 27001)
- Breach response timelines
- Third-party audit results
2. Update Legacy Systems
Outdated software is the No. 1 vulnerability exploited by ransomware actors. Migrate critical systems to modern, cloud-native platforms with encrypted backups.
3. Communicate Faster
Delay in notification often adds insult to injury. Have a crisis communication plan and legal templates ready before a breach happens.
4. Train Your Team
Human error still causes most breaches. Invest in ongoing phishing simulations, zero-trust access control, and password hygiene education.
Google’s $700M Settlement, Explained: Eligibility, Deadlines, and Payouts
Wells Fargo $33 Million Settlement: How Eligible Customers Can Claim Their Payout
AT&T Settlement: How Eligible Users Can Claim Up to $7,500 Before the Deadline